What Is Syn Flood Attack
Like the ping of death a SYN flood is a protocol attack. An SYN flood half-open attack is a type of denial-of-service DDoS attack which aims to make a server unavailable to legitimate traffic by consuming all available server resources.
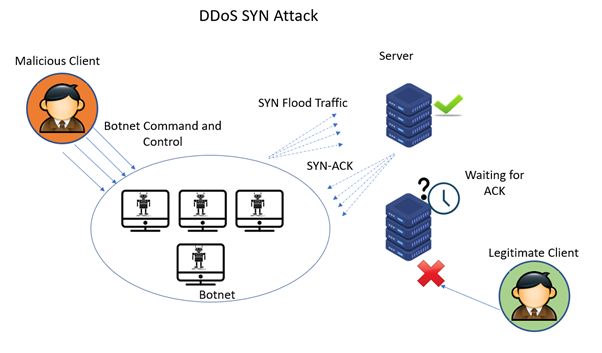
What Is Syn Synchronize Attack How The Attack Works And How To Prevent The Syn Attack Security Boulevard
A SYN flood is a form of denial-of-service attack in which an attacker rapidly initiates a connection to a server without finalizing the connection.
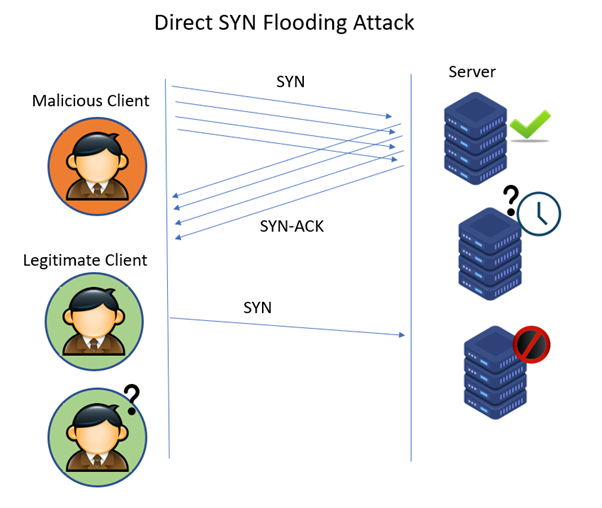
What is syn flood attack. SYN flood is a form of Transmission Control Protocol State-Exhaustion Attack which tries to consume connection state tables which are present in application servers IPS Intrusion Prevention Systems firewalls load balancers and other infrastructure components. Hackers send a large number of SYN packets to the server exhausting connection resources of the server and impacting normal user access. SYN flooding is a form of denial of service attack that can be launched on a computer server to overwhelm the server and not allow other users to access it.
A SYN flood is a type of TCP State-Exhaustion Attack that attempts to consume the connection state tables present in many infrastructure components such as load balancers firewalls Intrusion Prevention Systems IPS and the application servers themselves. What is SYN Flood attack and how to prevent it. This is a somewhat older form of attack and was quite popular for a time due to the relatively low resources needed to launch it.
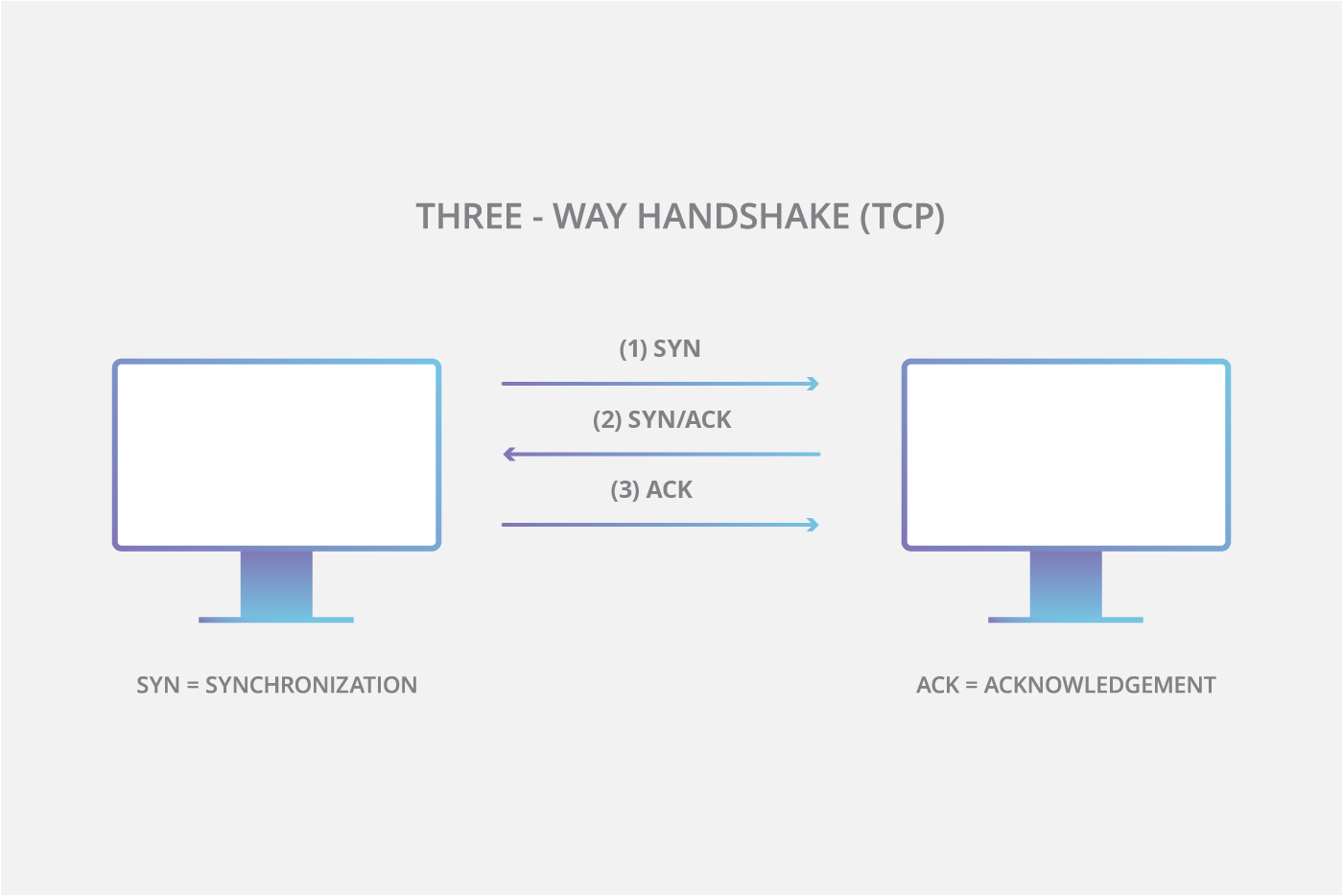
B responds with SYNACK segments to these addresses and then waits for responding ACK segments. The attacker sends a flood of malicious data packets to a target system. A TCP SYN Flood attack is categorized as DoS Denial of Service attackIt is undeniably one of the oldest yet the most popular DoS attacks that aim at making the targeted server unresponsive by sending multiple SYN packets.
SYN flood is a type of DDoS attack. SYN flood attack also known as the half-open attack is a protocol attack which exploits the vulnerabilities in the network communication to make the victims server. During the attack the TCP connections are sent at a much faster speed than the processing capacity of the machine causing it to saturate and ultimately slow down.
A SYN flood is a form of denial-of-service attack in which an attacker sends a progression of SYN requests to an objectives framework trying to consume enough server assets to make the framework inert to authentic activity. The intent is to overload the target and stop it working as it should. A SYN attack is a type of denial-of-service DoS attack in which an attacker utilizes the communication protocol of the Internet TCPIP to bombard a target system with SYN requests in an attempt to overwhelm connection queues and force a system.
By Jithin on October 14th 2016. By repeatedly sending initial connection request SYN packets the attacker is able to overwhelm all available ports on a targeted server machine causing the targeted device to respond to legitimate traffic. The hacker sends spoofed packets to your IP address from an open port on their computer attempting to connect.
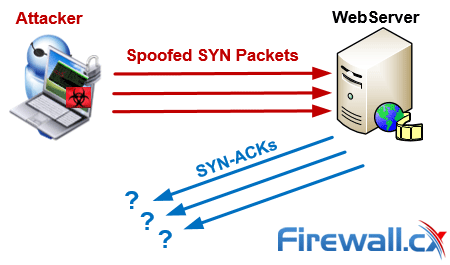
The server has to spend resources waiting for half-opened connections which can consume enough resources to make the system unresponsive to legitimate traffic. A SYN flood attack inundates a site with SYN segments that contain forged spoofed IP source addresses with non-existent or unreachable addresses. A SYN flood is a DoS attack.
A SYN flood half-open attack is a type of denial-of-service DDoS attack which aims to make a server unavailable to legitimate traffic by consuming all available server resources. SYN Flood is a type of DOS attack that floods a victims bandwidth with TCPIP connections requests but never completes them.

Tcp Syn Flood Attack In Telugu Youtube
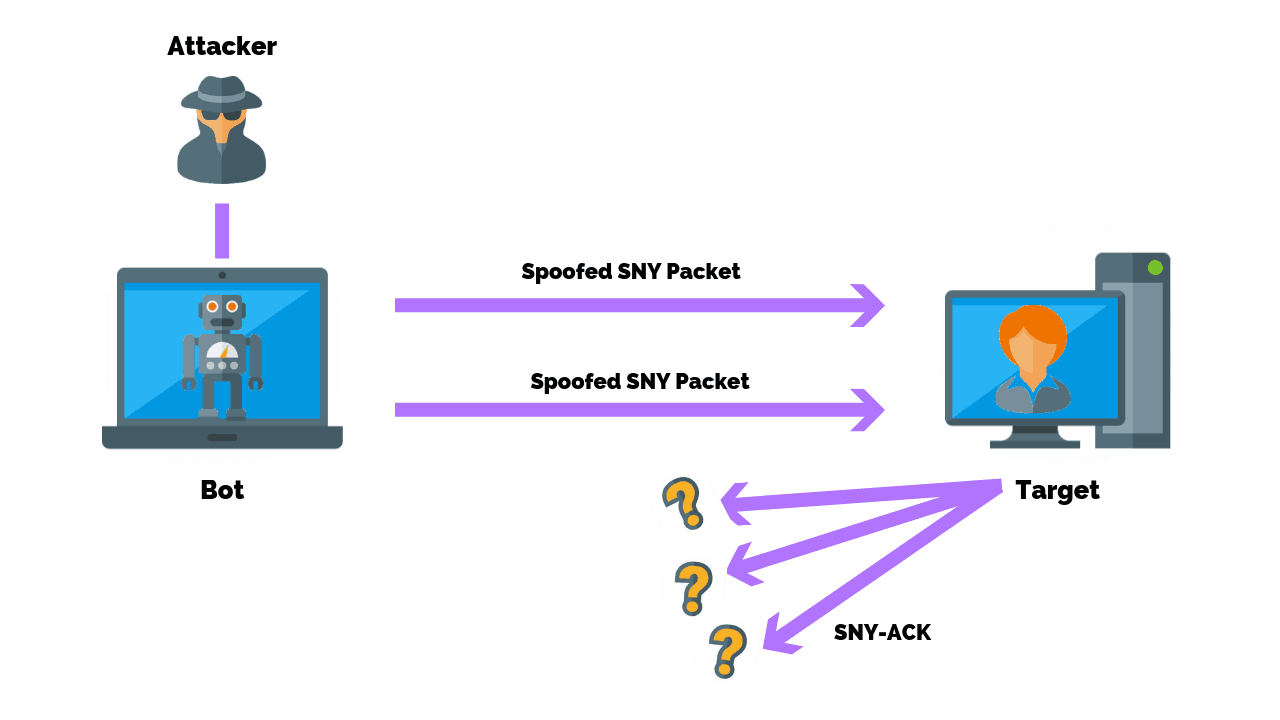
How To Prevent A Syn Flood Attack Purplesec
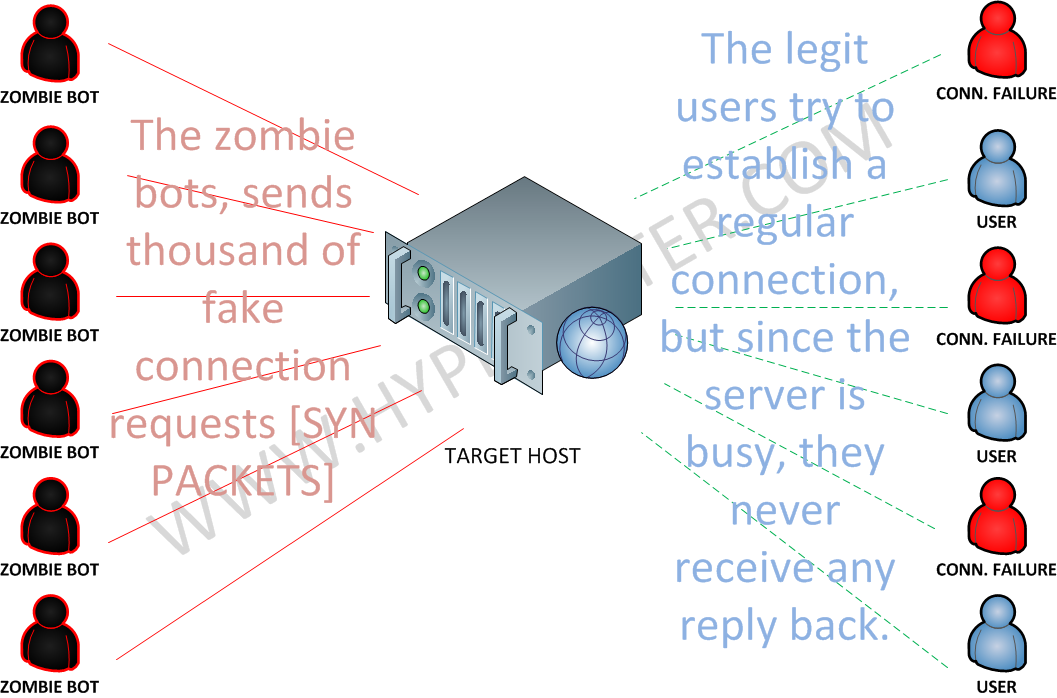
Tcp Attacks Hyperfilter Ddos Protection Solutions
Cisco Networking Vpn Security Routing Catalyst Nexus Switching Virtualization Hyper V Network Monitoring Windows Server Callmanager Free Cisco Lab Linux Tutorials Protocol Analysis Ccna Ccnp Ccie Page 66
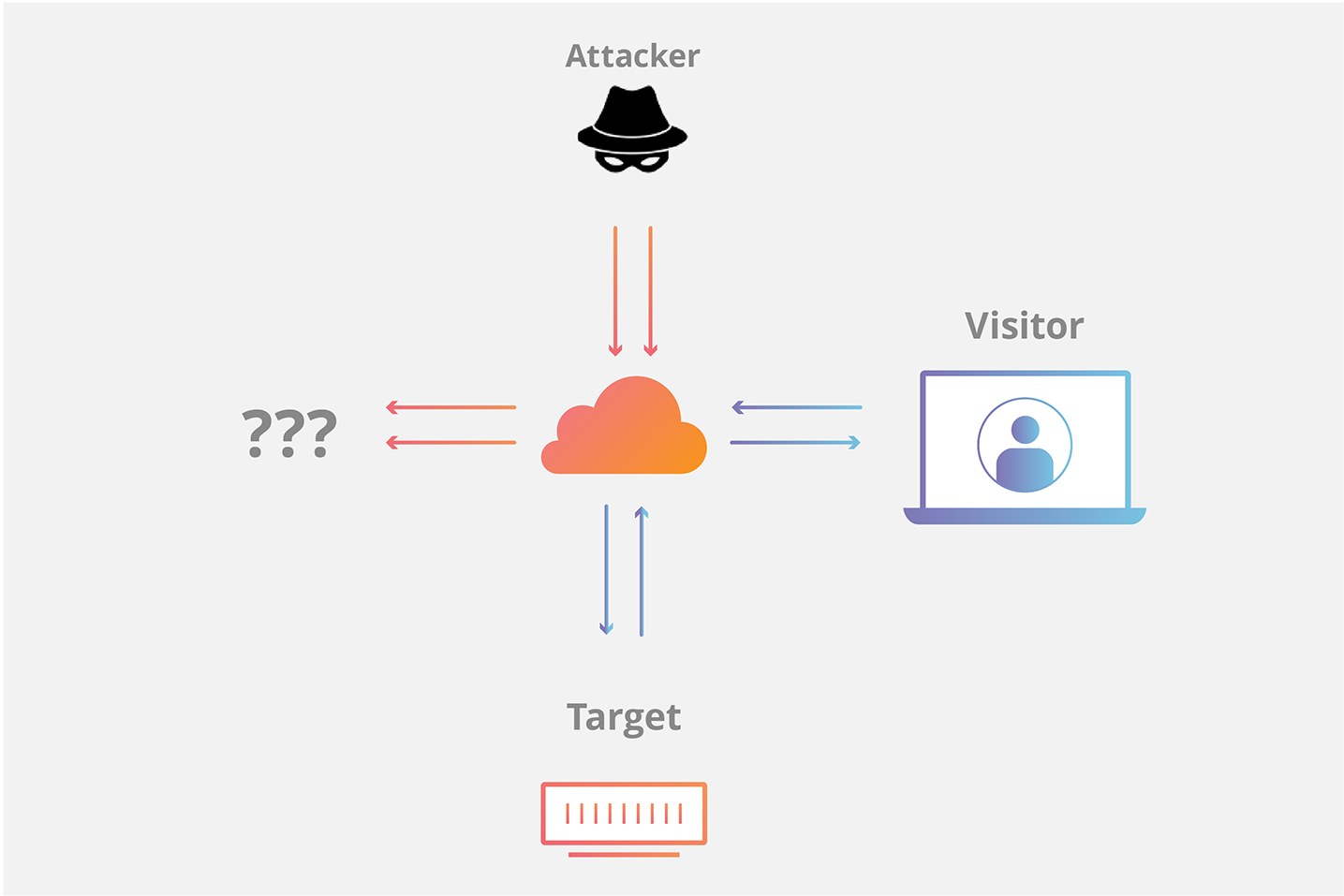
Syn Flood Ddos Attack Cloudflare

Tcp Syn Flood Attack Download Scientific Diagram

The Tcp Syn Flood Attack Hands On Lab Exercise On Tcp Syn Flood Attack Download Scientific Diagram

Syn Flood Attacks Aws Best Practices For Ddos Resiliency
Syn Flood Ddos Attack Cloudflare

Syn Dos Ddos Protection Routeros Mikrotik Documentation
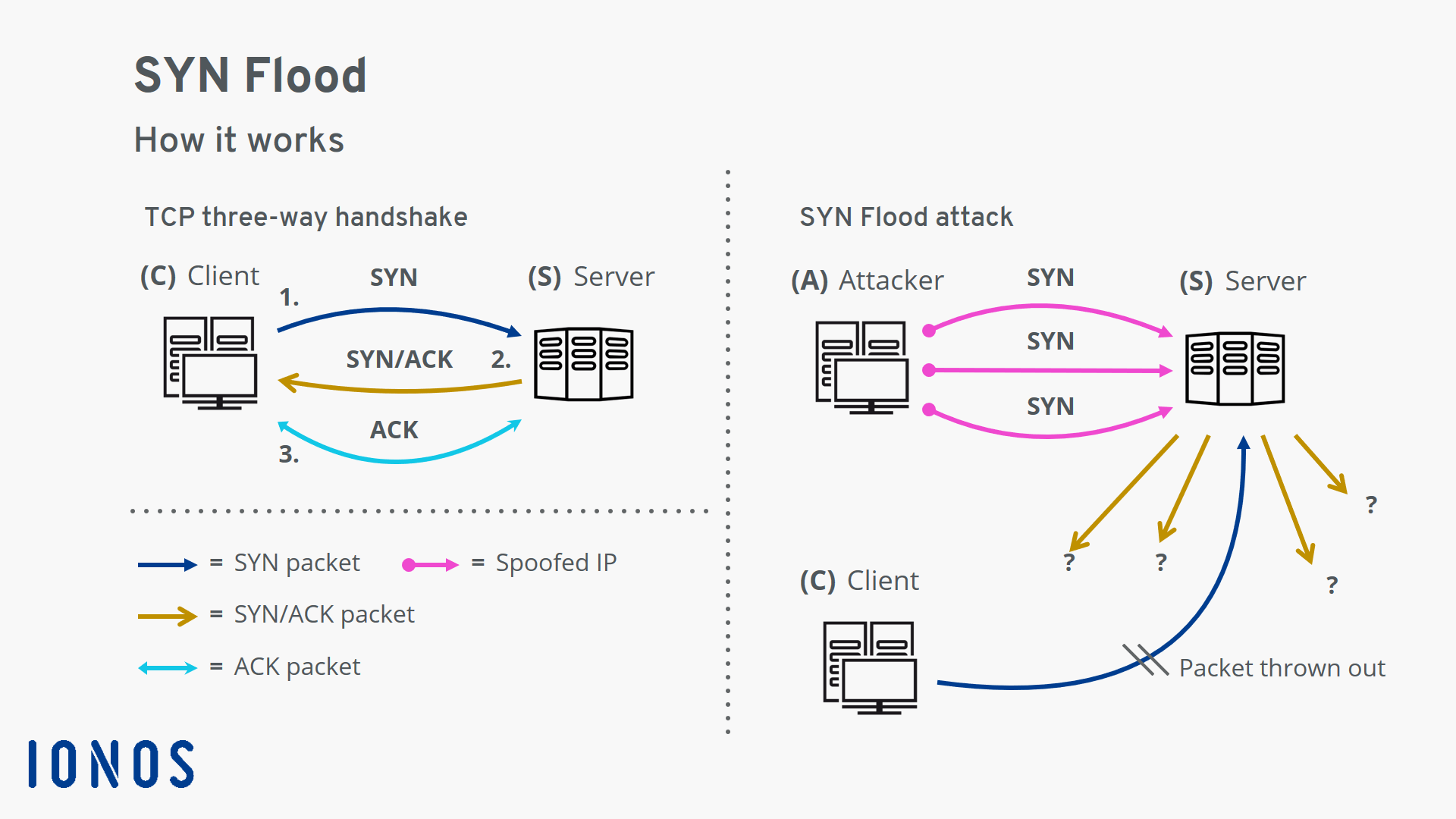
Syn Flood Attack Types Of Attack And Protective Measures Ionos

02 05 Syn Flood Attacks Youtube

Tcp Syn Flood Attacks Ccna Security 210 260 Certification Guide Book
What Are Tcp Syn Attacks Are They Similar To Ddos Attacks Quora
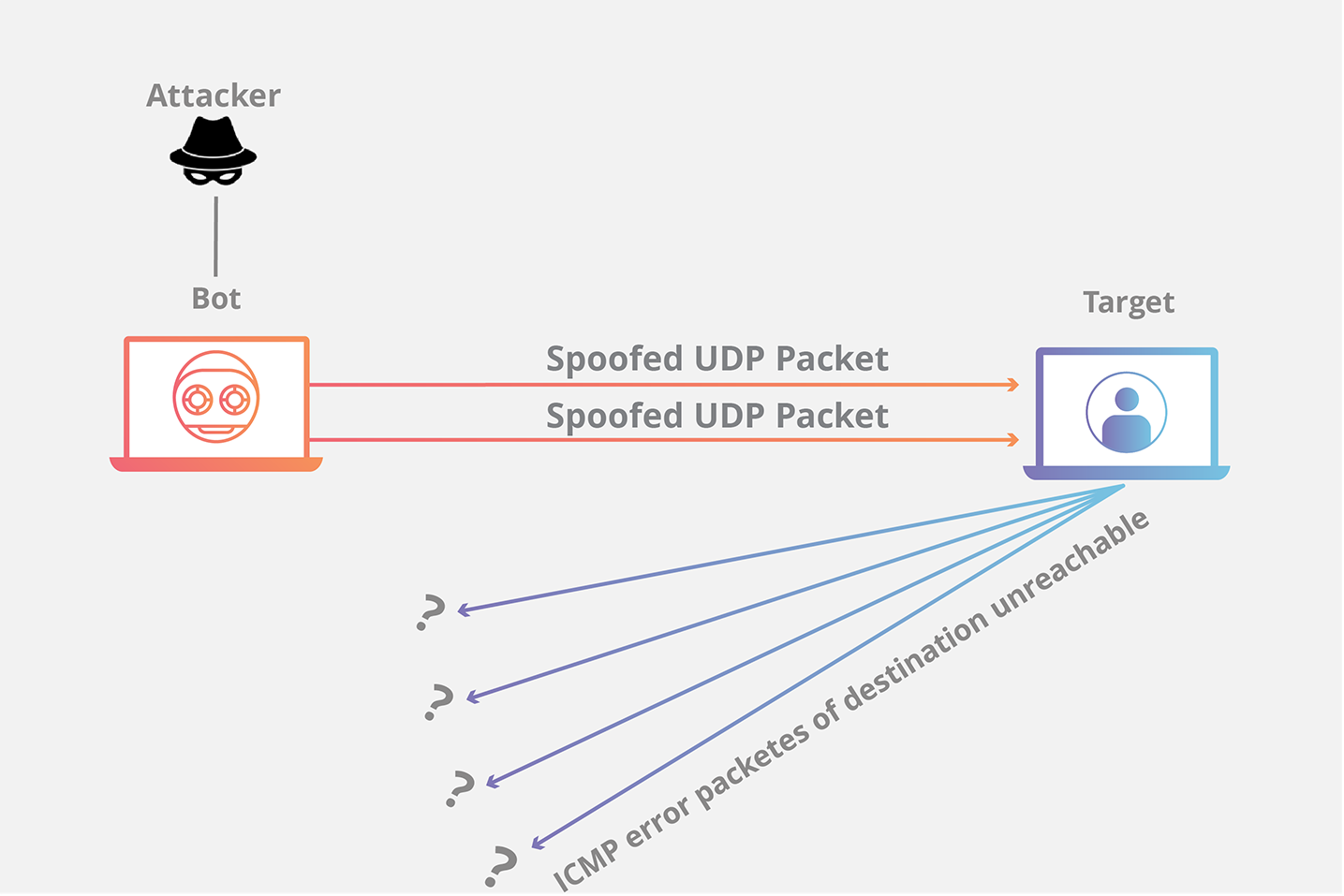
Udp Flood Ddos Attack Cloudflare
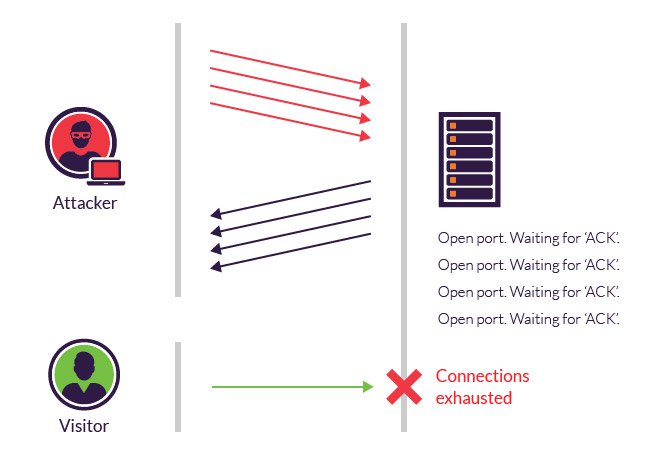
Tcp Sync Flood Attack Lte Telecomhall Forum
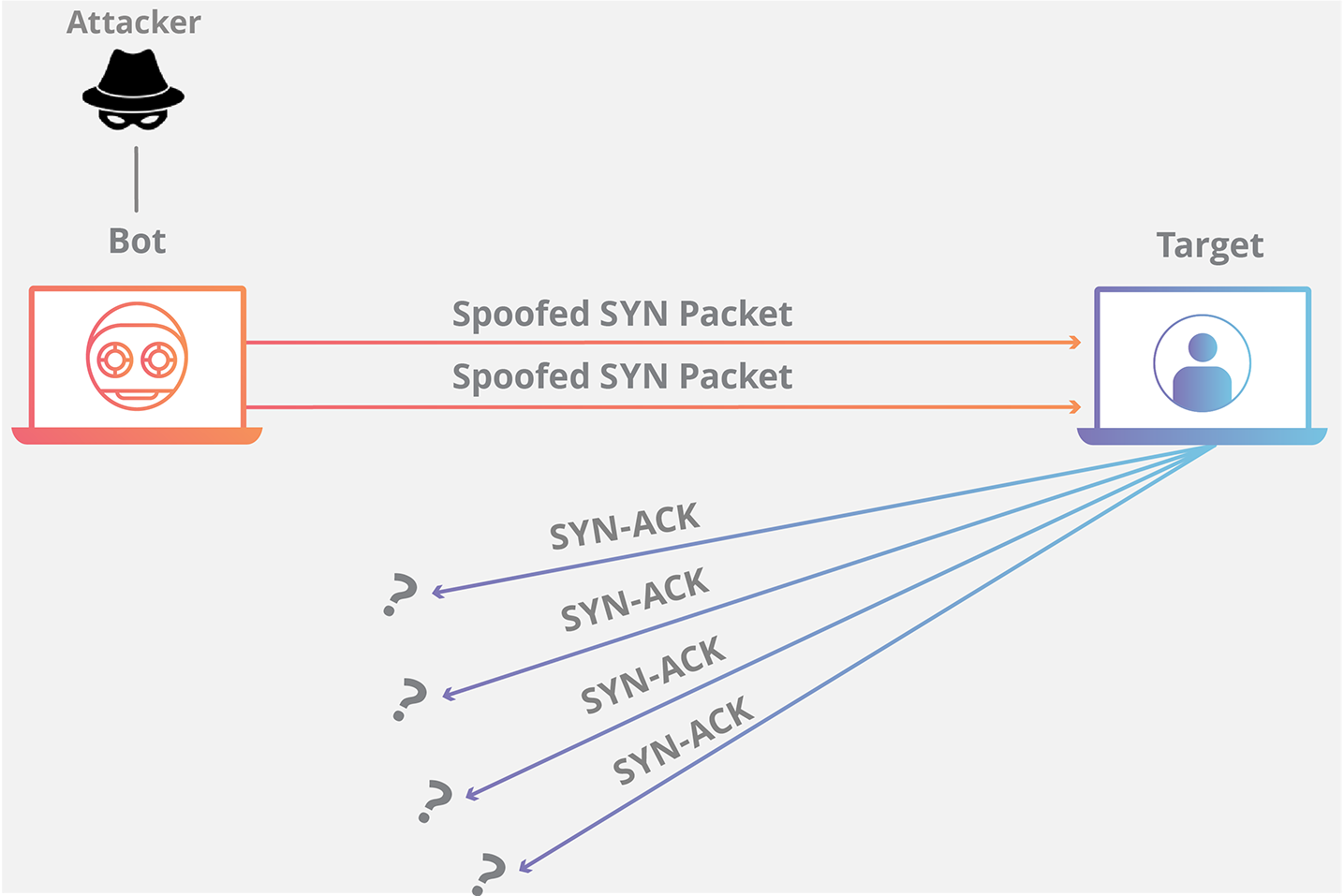
Syn Flood Ddos Attack Cloudflare

What Is Syn Synchronize Attack How The Attack Works And How To Prevent The Syn Attack Security Boulevard

Post a Comment for "What Is Syn Flood Attack"